The Ultimate Guide to Rate Limiting in System Design
Learn about rate limiting and how it protects your system from overload. Discover different rate limiting strategies, benefits, and implementation tips to manage traffic effectively
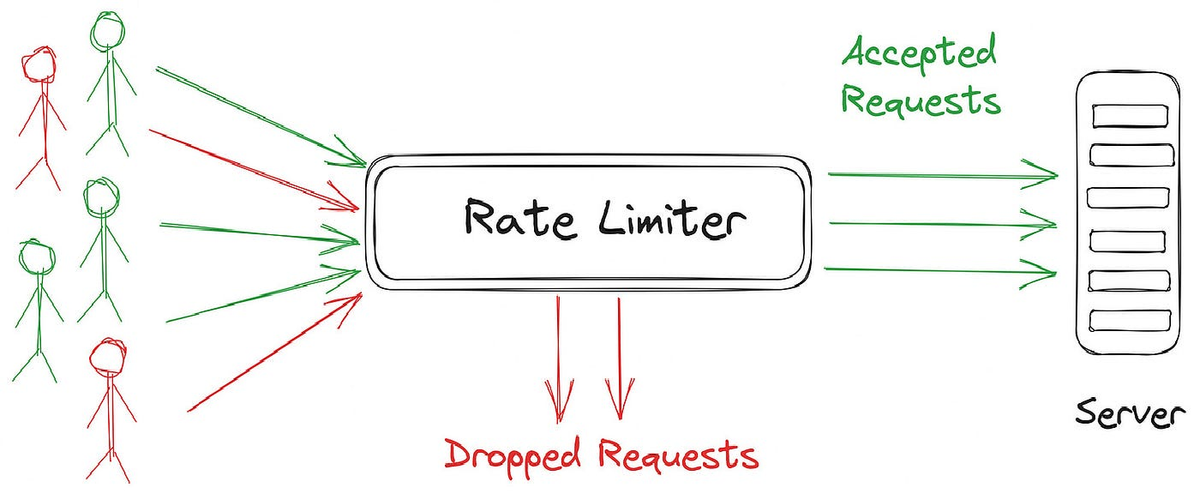
Ever had your favorite website slow to a crawl because of a sudden influx of users? Rate limiting is a technique designed to prevent exactly that scenario. By controlling how many requests a user or service can make in a given period, rate limiting helps maintain system performance and security. It's like having a traffic cop for your web traffic, ensuring that no single user or service can overload your system. Let’s dive into what rate limiting is, how it works, and how you can implement it effectively.
What is Rate Limiting?
Rate limiting in system design controls the number of requests a user or service can make to a system within a specified time frame. It prevents overloading servers, improves performance, and enhances security by managing traffic and ensuring fair usage.
It is essentially a way to control how frequently a user or service can make requests to your system. Imagine you’re at a popular coffee shop, and they only allow a certain number of people inside at a time to keep things manageable. Rate limiting does the same thing for your web services. It sets rules on the number of requests that can be made within a specific timeframe, such as 100 requests per minute. This helps prevent overloading your servers, ensuring smooth operation and fair access for all users.
Types of Rate Limiting
- Fixed Window Rate Limiting:
- This method sets a fixed time window, such as one minute or one hour, and limits the number of requests that can be made within that period. For example, you might allow 100 requests per minute.
- Ideal for straightforward applications where you need a simple way to enforce request limits without too much complexity.
- Sliding Window Rate Limiting:
- Unlike the fixed window method, the sliding window approach allows requests within a moving time frame. For instance, if you set a 1-minute sliding window, a user’s request count will be tracked over the past minute, not just within a fixed minute window.
- Useful for applications requiring more granular control and fair distribution of traffic, smoothing out bursty traffic patterns.
- Token Bucket Rate Limiting:
- This technique uses tokens to control the rate of requests. Tokens are added to a bucket at a constant rate. Each request consumes a token, and if the bucket is empty, further requests are denied or delayed. Tokens accumulate over time, allowing for bursts of traffic.
- Best for scenarios where occasional bursts are acceptable but overall traffic needs to be controlled.
- Leaky Bucket Rate Limiting:
- This method processes requests at a constant rate, smoothing out bursts by using a “bucket” that leaks at a steady rate. Excess requests that exceed the bucket’s capacity are delayed or rejected.
- Ideal for managing consistent traffic rates and handling sudden spikes without overwhelming the system.
Benefits of Rate Limiting
- Prevents Overload:
- By setting limits on request rates, rate limiting prevents your system from being overwhelmed by too many simultaneous requests, helping to maintain stability and prevent crashes.
- Improves Performance:
- It ensures that resources are used efficiently, preventing any single user or service from hogging system resources and degrading performance for others.
- Enhances Security:
- Rate limiting can thwart various types of attacks, such as brute-force attacks and denial-of-service attacks, by limiting the rate of requests from any single source.
How to Implement Rate Limiting in Your System
- Choose the Right Rate Limiting Method:
- Select a rate limiting strategy that fits your application’s traffic patterns and requirements. For instance, use token bucket rate limiting for applications needing flexibility with bursts of traffic.
- Configure Rate Limits:
- Define appropriate thresholds for request limits based on your system’s capacity and user needs. Ensure limits are set to balance protection without hindering legitimate use.
- Monitor and Adjust:
- Regularly monitor the performance and effectiveness of your rate limiting strategy. Make adjustments as necessary to address changing traffic patterns or new challenges.
Common Rate Limiting Challenges and Solutions
- Handling Burst Traffic:
- Challenge: Managing sudden spikes in traffic while enforcing rate limits can be tricky.
- Solution: Use methods like token bucket or leaky bucket rate limiting to handle bursts more gracefully and prevent immediate rejections.
- User Experience Impact:
- Challenge: Ensuring that legitimate users are not unfairly affected by rate limits.
- Solution: Implement adaptive rate limits based on user behavior or traffic patterns to minimize disruptions for genuine users.
- Bypassing Rate Limits:
- Challenge: Users might try to bypass rate limits through various methods.
- Solution: Employ techniques such as IP address monitoring and authentication to prevent circumvention and enforce limits more effectively.
Case Studies: Successful Rate Limiting Implementations
- Social Media Platform Enhancement:
- A social media platform implemented rate limiting to handle high traffic during major events. This approach prevented server overload and maintained smooth user interactions.
- API Protection:
- An API service used rate limiting to prevent abuse and ensure fair usage. This implementation reduced server strain and improved API performance for all users.
Future Trends in Rate Limiting
- AI and Machine Learning Integration:
- The future of rate limiting may involve AI and machine learning to predict traffic patterns and adjust limits dynamically for more precise control.
- Advanced Rate Limiting Techniques:
- Innovations in rate limiting will include more sophisticated methods for handling complex traffic patterns and improving user experience.
- Enhanced Security Measures:
- Future rate limiting solutions will focus on integrating advanced security features to protect against evolving threats and ensure robust protection.
Rate limiting is a crucial tool for managing traffic and ensuring system stability. By controlling the rate at which requests are processed, you can prevent overload, enhance performance, and improve security. Explore different rate limiting strategies and implement them based on your system’s needs to achieve optimal results. Feel free to share your experiences or ask questions about rate limiting in the comments!




